A small script for export Computers BitLocker Recovery Information from Active Directory to csv file.
This script generates a CSV file with computer names and BitLocker Recovery Keys:
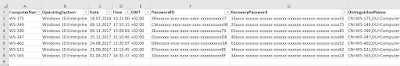
ComputerName;OperatingSystem;Date;Time;GMT;PasswordID;RecoveryPassword;DistinguishedName
ComputerName;OperatingSystem;Date;Time;GMT;PasswordID;RecoveryPassword;DistinguishedName
Requirement of the script:
- Active Directory PowerShell Module
- Needed rights to view AD BitLocker Recovery Info
Example of usage:
- Active Directory PowerShell Module
- Needed rights to view AD BitLocker Recovery Info
Example of usage:
[PS].\Get-ADComputers-BitLockerInfo.ps1
[PS].\Get-ADComputers-BitLockerInfo.ps1 -OU "OU=Computers,OU=IT Department,DC=myDomain,DC=com"
Links for download
Example of reports
in CSV
in Excel
#.\Get-ADComputers-BitLockerInfo.ps1 #---------------------------------------------------------[Initialisations]-------------------------------------------------------- [CmdletBinding()] Param( [Parameter(Mandatory=$false, HelpMessage="Enter OU, example: OU=Computers,OU=ITDep,DC=contoso,DC=com", ValueFromPipelineByPropertyName=$true)] [string]$OU, [Parameter(Mandatory=$false, HelpMessage="Enter path for log file, example: C:\Scripts", ValueFromPipelineByPropertyName=$true)] [string]$LogFilePath = ".\", [Parameter(Mandatory=$false, HelpMessage="Enter log file Name", ValueFromPipelineByPropertyName=$true)] [string]$LogFileName = "BitLockerInfo_$(Get-Date -f 'yyyy-MM-dd').csv" ) #----------------------------------------------------------[Declarations]---------------------------------------------------------- Import-Module ActiveDirectory #To separating fields for report $strDelimiter = ";" if (-Not (Test-Path -PathType Container $LogFilePath)){ $LogFilePath = New-Item -ItemType Directory -Force -Path $LogFilePath } if ($LogFilePath.Substring($LogFilePath.Length-1) -eq "\" -or $LogFilePath.Substring($LogFilePath.Length-1) -eq "/"){ } else { $LogFilePath = $LogFilePath + "\" } $LogFile = $LogFilePath + $LogFileName #Report file $LogFile if (Test-Path $LogFile){ #Remove-Item $LogFile Clear-Content $LogFile } else { $LogFile = New-Item -Path $LogFilePath -Name $LogFileName -ItemType File } write-host write-host "Script start" $(Get-Date) write-host #Set scope #Get computers info if ($OU -ne "") { Write-Host "Organizational Unit:" $OU $Computers = Get-ADComputer -Filter 'ObjectClass -eq "computer"' -Property * -SearchBase $OU } else { Write-Host "Domain:" $env:userdnsdomain $Computers = Get-ADComputer -Filter 'ObjectClass -eq "computer"' -Property * } write-host "Report File Path:" $LogFile #Write report header $strToReport = "ComputerName" + $strDelimiter + "OperatingSystem" + $strDelimiter + "Date" + $strDelimiter + "Time" + $strDelimiter + "GMT" + $strDelimiter + "PasswordID" + $strDelimiter + "RecoveryPassword" + $strDelimiter + "DistinguishedName" Add-Content $LogFile $strToReport #Get BitLocker Recovery Info #Write report foreach ($Computer in $Computers) { $BitLockerObjects=(Get-ADObject -Filter {objectclass -eq 'msFVE-RecoveryInformation'} -SearchBase $Computer.DistinguishedName -Properties msFVE-RecoveryPassword) foreach ($BitLockerObject in $BitLockerObjects) { #The name of the BitLocker recovery object incorporates a globally unique identifier (GUID) and date and time information, #for a fixed length of 63 characters. The form is: <Object Creation Date and Time><Recovery GUID> #For example: #2005-09-30T17:08:23-08:00{063EA4E1-220C-4293-BA01-4754620A96E7} #$BitLockerObject.Name $strComputerDate = $BitLockerObject.Name.Substring(0,10) $strComputerTime = $BitLockerObject.Name.Substring(11,8) $strComputerGMT = $BitLockerObject.Name.Substring(19,6) $strComputerPasswordID = $BitLockerObject.Name.Substring(26,36) $strComputerRecoveryPassword = $BitLockerObject.'msFVE-RecoveryPassword' $strToReport = $Computer.Name + $strDelimiter + $Computer.OperatingSystem + $strDelimiter + $strComputerDate + $strDelimiter + $strComputerTime + $strDelimiter + $strComputerGMT + $strDelimiter + $strComputerPasswordID + $strDelimiter + $strComputerRecoveryPassword + $strDelimiter + $Computer.DistinguishedName Add-Content $LogFile $strToReport } } write-host write-host "Script end" $(Get-Date) write-host
Links for download

Thanks for the comment.
ReplyDeleteYou needed rights to view AD BitLocker Recovery Info.
Read access to msFVE-RecoveryInformation objects.
@xknucklezx, do you have these rights?
the script will not work for AD without attributes like msFVE-RecoveryInformation and msFVE-RecoveryPassword, right?
ReplyDeleteYes. In AD attributes msFVE-RecoveryInformation and msFVE-RecoveryPassword stored BitLocker recovery info.
DeleteYou needed rights to view AD BitLocker Recovery Info (read AD attributes msFVE-RecoveryInformation and msFVE-RecoveryPassword)
Perfect
ReplyDeleteThank you